Adding tasks to a Microsoft Sentinel incident via REST API
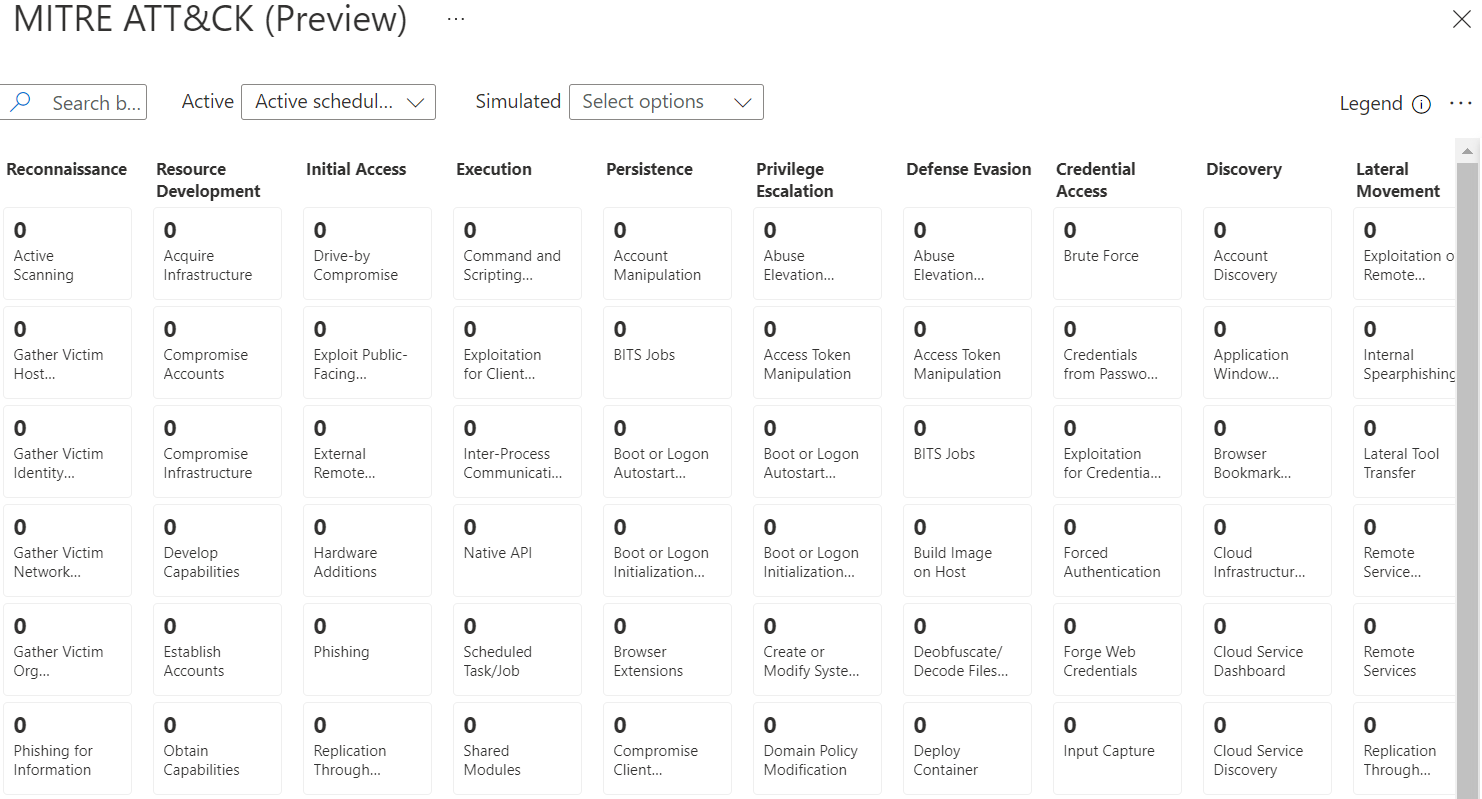
Introduction The new ability to add tasks to an incident in Microsoft Sentinel is one of the best new features IMHO. It takes one big step forward in being able to completely handle the complete incident investigation within Microsoft Sentinel. As of right now, you can either run an automation rule or use the Microsoft […]